Collecting logs from Oracle Cloud¶
You can collect logs from Oracle Cloud Infrastructure (OCI).
More about OCI Logging can be found here.
For LogMan.io Collector configuration, you will need to:
- Generate a new API key together with new public and private keys in the OCI console
- Create a new search query for the API requests
Generating API key in OCI Console¶
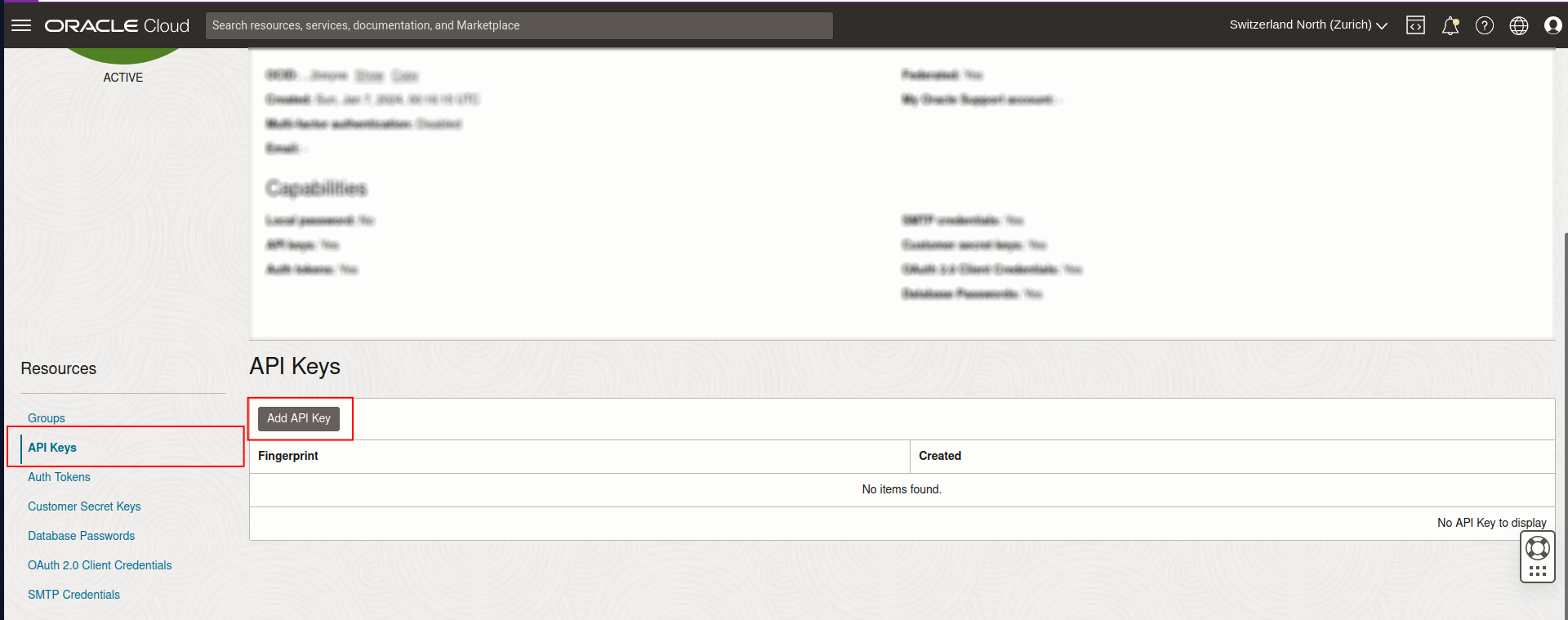
-
Log in to your OCI Console.
-
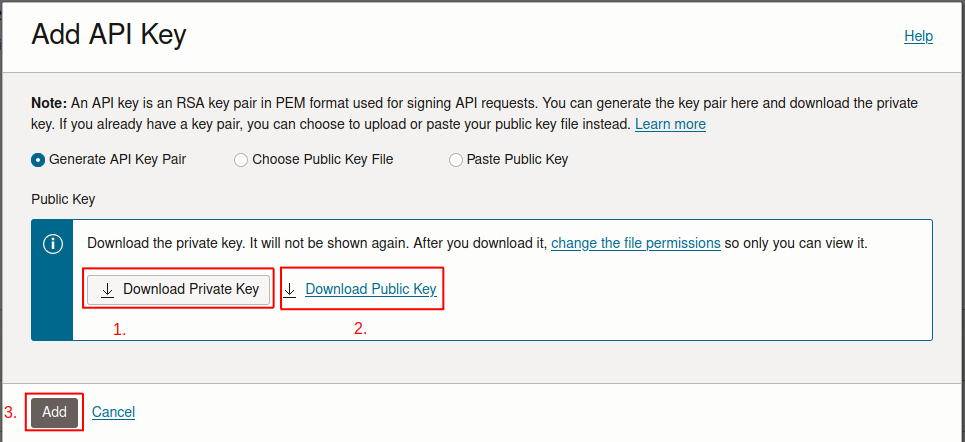
Make sure Generate API Key Pair is selected. Click Download Private Key and then Download Public Key. Then, click Add.
-
A configuration file with all the credentials you need will be created. Paste the contents of the text box into the
data/oci/configfile.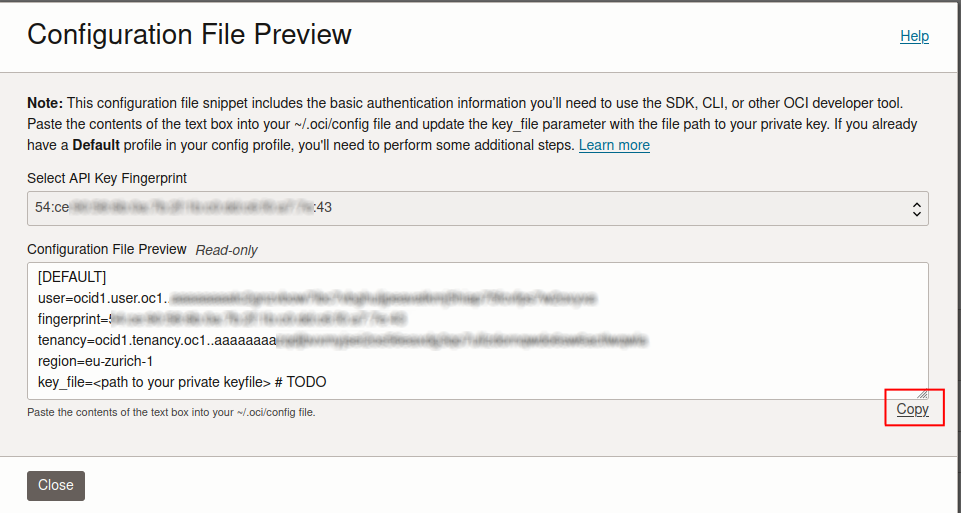
-
Fill out
key_filewith the path to your private key file.
Important
Never share your private key with anyone else. Keep it secret in its own file. You might need to change the permissions of the public and private keys after downloading them.
How does the requesting process work?
The private and public keys are part of an asymmetric encryption system. The public key is stored with Oracle Cloud Infrastructure and is used to verify the identity of the client. The private key, which you keep secure and never share, is used to sign your API requests.
When you make a request to the OCI API, the client software uses the private key to create a digital signature for the request. This signature is unique for each request and is generated based on the request data. The client then sends the API request along with this digital signature to Oracle Cloud Infrastructure.
Upon receiving the request, Oracle uses the public key (which it already has) to verify the digital signature. If the signature is valid, it confirms that the request was indeed sent by the holder of the corresponding private key (you) and has not been tampered with during transmission. This process is crucial for maintaining the integrity and authenticity of the communication.
The private key itself is never sent over the network. It stays on your client-side. The security of the entire process depends on the private key remaining confidential. If it were compromised, others could impersonate your service and send requests to OCI on your behalf.
Logging Query Language Specification¶
Please refer to the official documentation for creating new queries.
You will need the following information:
- Compartment OCID
- Log group OCID
- Log OCID
Logging Query Example
search "<compartment_OCID>/<log_group_OCID>/<log_OCID>" | where level = 'ERROR' | sort by datetime desc
Configuration¶
Below is the required configuration for LogMan.io Collector:
input:Oracle:OCIInput:
oci_config_path: ./data/oci/config # Path to your OCI configuration file (required)
search_query: search '<compartment_OCID>/<log_group_OCID>/<log_OCID>' | where level = 'ERROR' # (required)
encoding: utf-8 # Encoding of the events (optional)
interval: 10 # Number of seconds between requests to OCI (optional)
output: <output_id> # (required)
Development¶
Warning
LogMan.io Collector Oracle Source is built on OCI integration for API which uses synchronous requests. There might be some problems when there is heavy TCP input.